
Cloud computing has become very popular in the information technology field in recent times. It is popular due to the ease of managing hardware and infrastructure without owning them.
There are many cloud service providers in the market, and Amazon Web Services leads all of them by providing more than 200 cloud computing services. While architecting any software product, we must consider many more cases to design scalable, secure, and efficient products.
AWS is suggesting the following six pillars for a well-architected application:
Security
Performance
Reliability
Sustainability
Operational Excellence
Cost Optimization
In this article, I would like to discuss cost optimization on AWS. AWS offers a range of tools, best practices, and strategies that help you optimize your workload/service costs.
Following are some key steps and considerations for AWS cost optimization:
Rightsized Resources/Workloads instances.
Use Reserved and Spot Instances.
Consider Saving Plans.
Use AWS Cost Explorer and Budgets.
Serverless Architectures.
Those are the few common steps that most of the Software Engineering team is aware of and taking care of for cost optimization in AWS. So, let’s discuss some unusual steps and considerations to optimize AWS cost. It will be in multiple parts of the blog series, and the targeted audience is AWS practitioners.
Cost of data Transfer:
In general, while architecting software products using AWS, we fail to spot the data transfer cost; however, considering a few data transfer decisions can help save some bucks from monthly AWS billing.
AWS S3:
Data transfer between one region to another region from the S3 bucket will incur the highest cost from the S3 bucket data transfer perspective. So, design your architecture so minimal data transfer between multiple areas is required.
EC2 or IP-based Workloads:
Data transfer from the Internet to AWS is free, but transfer from AWS to the Internet is chargeable. So, avoid communicating internal workloads using Public IP/Elastic IP. Use private IP instead. (For free data transfers).
VPC Endpoints allow connectivity between AWS services over private networking and can be used to reduce public data transfer and NAT gateway costs. We can use the Gateway VPC endpoint from private subnet EC2 instances to access S3 bucket data. Gateway VPC endpoints have no hourly charges and support S3 and DynamoDB.
Route 53
Use the TTL value wisely. A low TTL value (e.g., 15 seconds) will expire the cache quickly to avoid stealing data. However, It will increase the traffic to Route53, costing you more.
Create alias records, when possible, data traffic using alias records mapped to resources provided at no cost. Resources like., Elastic Load Balancer, Elastic Beanstalk Environments, API Gateway, VPC Endpoints, S3 website Buckets, CloudFront.
CloudFront
The cost of data out per edge location varies; hence have to select/reduce the number of edge locations. It will help to reduce the cost of outside data transfer through CloudFront. 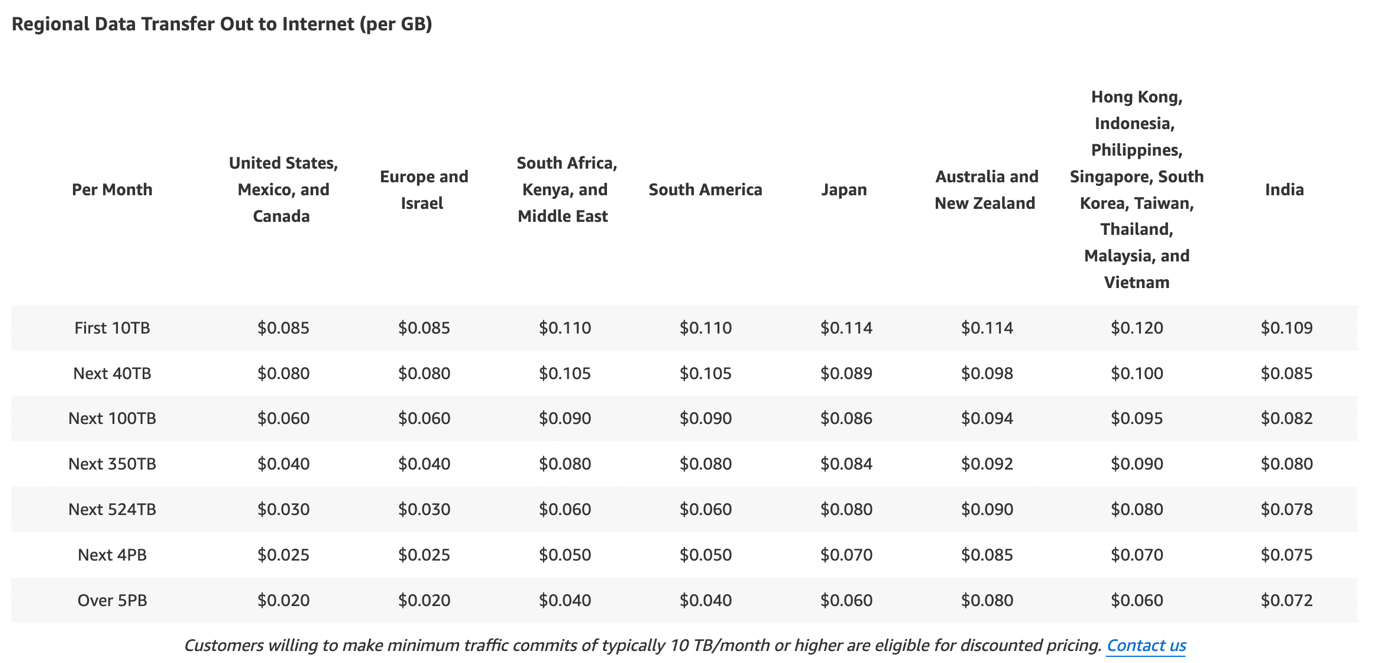
Embracing unconventional strategies for AWS cost optimization can set your cloud infrastructure on a more efficient and cost-effective trajectory. By thinking beyond the usual cost-cutting measures and diving into the depths of your AWS resources and usage patterns, you open new avenues for savings and improved resource allocation.
Cost optimization steps for AWS S3 object encryption cost.
Key Management Service (KMS)
We know that KMS is used to keep and manage keys to encrypt and decrypt data at rest.
AWS-owned key – Free.
AWS managed key - No monthly fee; however, Per-use/API call fee.
The customer ordered the key – Monthly and Per-use/API call fee.
S3 Object Encryption Cost Optimization for Server-side Encryption using AWS Managed Key (SSE-KMS) using S3 Bucket Keys.
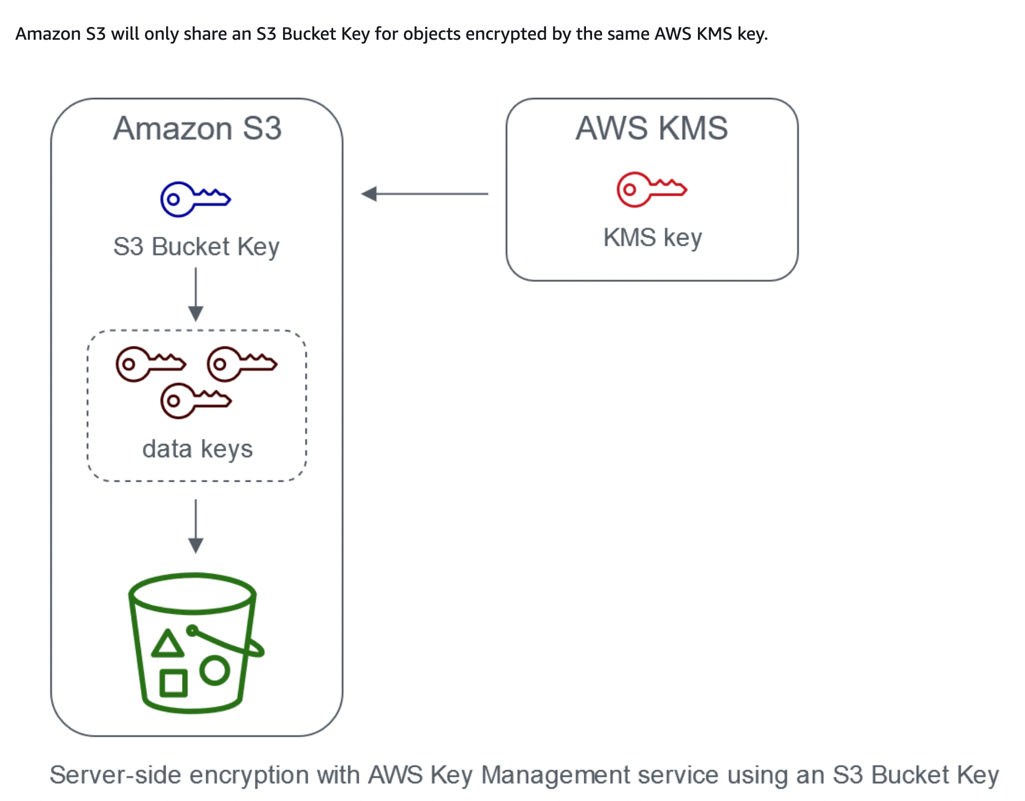
Using S3 bucket-level key for SSE-KMS, we can reduce AWS KMS request costs by up to 99 per cent by decreasing the request traffic from Amazon S3 to AWS KMS. When configuring AWS KMS keys using SSE-KMS, we can configure the bucket to use an S3 Bucket Key for SSE-KMS on new objects.
Using the AWS CLI, enable default bucket encryption with SSE-KMS and an S3 Bucket Key. 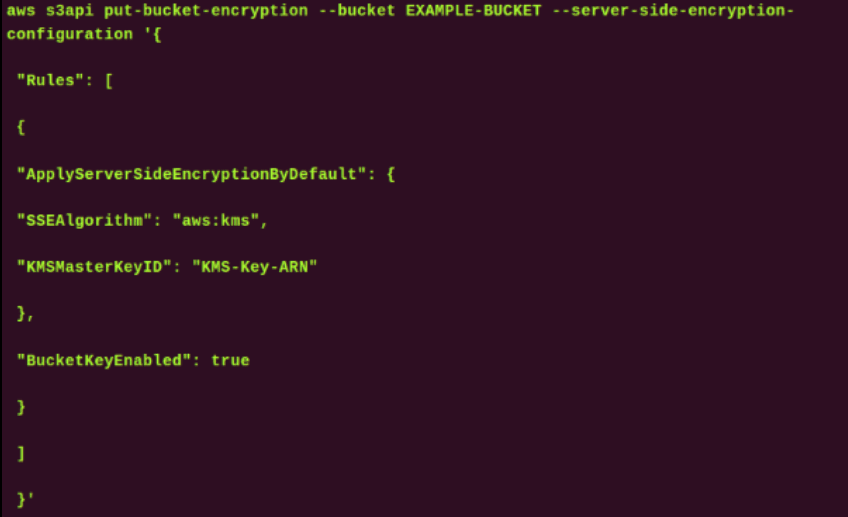
We can configure S3 Bucket Key using SDK, REST API, CloudFormation and AWS Console. Check AWS Documentation for more detail.
When S3 Bucket Key is enabled for the source/destination bucket, the encryption context will be the S3 ARN and not the object ARN, like., arn:aws:s3:::bucket_ARN. You need to update your IAM policies to use the bucket ARN for the encryption context.
A unique bucket-level key is generated for each requester to ensure an AWS KMS CloudTrail event captures the requester. Existing objects from the S3 bucket will not use S3 Bucket Key. We can use a COPY operation to configure an S3 Bucket Key for living things. During the COPY operation, we need to add the x-amz-server-side-encryption-bucket-key-enabled request header with a true or false value.
In wrapping up our exploration of unconventional strategies for AWS cost optimization, we've delved into a realm of possibilities beyond surface-level tactics. Part 2 has expanded upon the foundation laid in Part 1, presenting you with even more innovative ways to streamline your AWS expenses and resource utilization.
That’s it from the blog. In the next part of the AWS cost optimization blog series, let's discuss more exciting steps. Please follow Aspire Softserv to keep up to date about upcoming Blogs or Contact us to solve your business problems with our expert team.



